Bitcoin just pulled one of its classic moves-dipping on the “news” after soaring on the “rumor.”
Related Posts
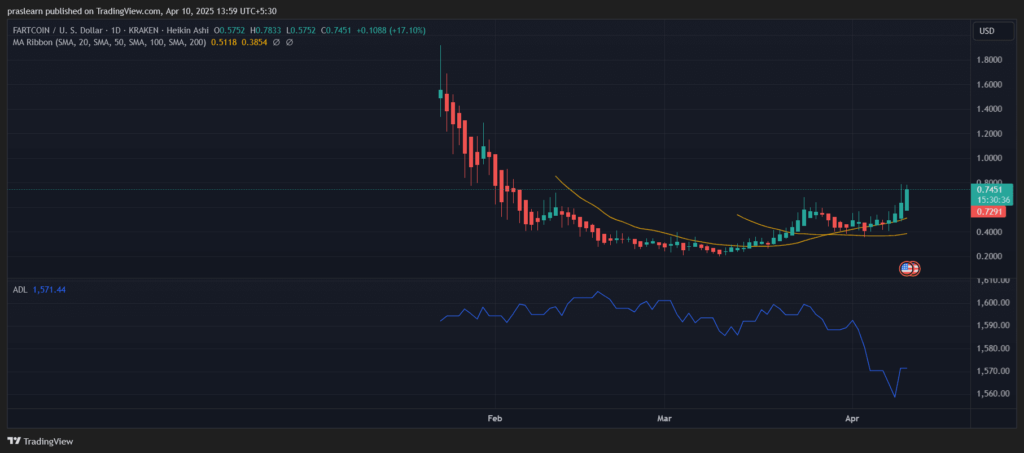
Fartcoin to Reach $5? Chart Signals Point to a Potential Explosion

Surprise! Surprise — Trump Reverses Course on Tariffs… But Why?
Surprise! Surprise — Trump Reverses Course on Tariffs… But Why?

Created using Microsoft Designer Image Generator and Canva
Hot Theme to Make Memes On — Trump Tariffs
There’s no doubt about it — anyone into making memes or comics has struck gold with the latest episode in Donald Trump’s “Tariff Series.”
I’ve personally created several memes and visuals capturing the market chaos sparked by President Trump’s aggressive tariff policy.

Created using Canva
Yes… he went all out with his harsh tariff announcements, leaving markets in flames — not just in the US, but in Japan, China, Taiwan, Europe, and beyond.
As one of my memes shows, Trump’s tariff shots have wounded global markets.

Created using Canva
His tariff punches were the nightmare scenario for economies around the world!

Created using Canva
Just yesterday, I had finished writing about the deep dive in crude oil markets — a clear sign of recession fears taking hold.
Markets in Panic Mode: Crude Oil Collapse Reflects Global Economic Jitters
The drop reflected worries about declining economic activity such as manufacturing and production, which in turn drags down the price of oil.

Created using Canva
Trump Tones It Down: A 90-Day Pause Brings Relief

Created using Microsoft Designer Image Generator and Canva
But today, the tide is turning. Markets are rallying after Trump announced a 90-day pause on his harsher tariff plans targeting trading partners.
He has now opted to impose just a 10% tariff on imports from most countries. Markets are breathing easier — green candles are back, and it feels like the sun has finally come out after the storm of Trump’s earlier aggression.
Still, the change raises eyebrows. Why the sudden shift?
While the 10% tariff remains for most countries, the 125% tariff on Chinese imports stays unchanged. In retaliation, China will slap 84% tariffs on US imports.
Trump reverses course on reciprocal tariffs, announces 90-day ‘pause’ for all but China
So clearly, the trade war hasn’t been called off — just dialed down for now.
The real reason behind the backpedaling? The Bond Markets.
Why the U-Turn? Clues Lie in the Bond Market Meltdown
As I’ve explained in earlier posts, during economic uncertainty, investors rush to “safe haven” assets like the USD and US bonds. But lately, something’s changed — investors have been selling off US bonds.

Tradingview>>Sell off in 2 year US Bond Market and price decline

Tradingview>> Increase in yields from 3.45% to 4.047%

Tradingview chart>> Sell off in 10 year US Bond Market and price decline

Tradingview>> Increase in US 10 year Bonds from 3.8% to 4.5%.
This sell-off has caused yields on 2-year and 10-year US bonds to rise as their prices drop. That’s a warning sign: investors are losing confidence in the US economy.
Trump says 90-day pause on reciprocal tariffs for all except China>>
And that’s dangerous.
An escalating trade war could lead to a full-blown economic collapse. A mass bond sell-off means the US government must pay back bondholders with interest — putting more pressure on banks, the Treasury, and the entire financial system.
The risk? A bond market meltdown, followed by a banking crisis and drained USD reserves.
Faced with this ticking time bomb, Trump had to pivot.
So yes, the tariff madness has been toned down, but make no mistake — it hasn’t ended.
The meme-worthy drama continues. Stay tuned!
My article can also be found in these platforms I post my content on-:
Hive — https://ecency.com/hive-150329/@mintymilecan
Publish0x — https://www.publish0x.com/@greenchic
Medium — https://medium.com/@kikctikcy
t2World — https://app.t2.world/
Surprise! Surprise — Trump Reverses Course on Tariffs… But Why? was originally published in Coinmonks on Medium, where people are continuing the conversation by highlighting and responding to this story.

$124M Stolen — The March 2025 Crypto Crime Report
$124M Stolen — The March 2025 Crypto Crime Report

In March 2025, $124 million was lost to crypto crimes across 25 separate incidents. Of that amount, approximately $4.5 million was recovered, bringing the net effective loss to just over $119 million.
Most of the losses were attributed to hacks, with smart contract exploits taking center stage, accounting for $19,4 million across eight major incidents. Private key exploits followed, with $15.3 million lost across four cases.
What truly made March 2025 stand out, however, was the cluster of eclectic and headline-worthy crypto crime stories.
Beyond the ongoing hunt for the $1.43 billion stolen from Bybit, March 2025 also saw the exposure of a MOVE market maker manipulating the token, Coinbase users collectively losing over $46 million to phishing scams, and revelations that a Coinbase employee may have accessed user data to deploy phishing attacks. On top of that, there was the shocking revelation of a North Korean mole who successfully infiltrated the crypto space, Hyperliquid teetering on the edge of liquidation, the emergence of a new type of smart contract exploit, and even a hacker getting scammed.
We’ve cherry-picked some of the most impactful stories for our March 2025 crypto crime report. Now, let’s dive in.
MARCH 2025 I Crypto Crime Data






Infiltrated North Korean Hacker Behind Radiant Capital Breach and Foiled 1inch Attack
At the beginning of 2024, an unassuming blockchain security researcher named Nick L. Franklin quietly made his debut on Crypto Twitter.

Armed with deep expertise in blockchain security, a relentless drive to make the crypto space safer, and a generous spirit that led him to support fellow security researchers and crypto builders, Nick quickly built a thriving community.
Over the past year, he has freely engaged with the co-founders of top DeFi protocols, forged friendships with leading security researchers from prominent blockchain security firms.
But all of this came to a screeching halt on March 26, 2025, when Anton Bukov, co-founder of 1inch, exposed a shocking truth: the researcher who had generously shared his time, security insights on exploits, and advice on securing protocols was, in fact, a fraud.

He shared his exchange with Nick, in which he asked him to review an alleged security report he had prepared for 1inch. However, Anton immediately grew suspicious when Nick sent him an APP file that could potentially compromise his device. When confronted, Nick abruptly banned Anton — prompting him to sound the alarm on Twitter.

The crypto community immediately grew suspicious that a North Korean agent was behind this profile, as they have been known to silently infiltrate the cryptosphere to better execute their heists.
That same day, Tanuki42, a blockchain security researcher at ZeroShadow, was able to link Nick’s activities to the Radiant Capital hack!
Tanuki investigated addresses used by Nick and stumbled upon one he had used to request testnet ETH tokens back in August 2024: 0xECe8eBB0F1c31bE085C1Dd899299f01c0aEC95A1.

After reviewing the GitHub repository compiled by MetaMask security researcher Taylor Monahan, which lists blockchain addresses linked to DPRK activities, Tanuki discovered a match. One of the addresses had been used in testing for the $50 million Radiant hack in October 2024.
A hack that was attributed to the DPRK APT group AppleJeus (also known as Citrine Sleet and UNC4736).
The next day, security researcher pcaversaccio analyzed the malicious app file used in the attempted attack on 1inch through Nick Franklin. Based on his findings, he alleged that the attack was “part of a broader deception and exploitation attempt [and] can be attributed with high confidence to the AppleJeus/Citrine Sleet DPRK team.”

Nick that could be the pseudo behind which one or more Applejeus agent hidden, was not only implicated in the Radiant Capital hack, they also built for themselves a gigantic and long-spanned social engineering trap destined to entrap, based on Nick screening of past interactions, at least 1inch, OpenZeppelin and Hyperliquid.
An intriguing detail is that Nick also seemed to have pursued a kind of side quest?
After announcing on Twitter in August 2024 that they wanted to launch their own DeFi project, a liquidity protocol called Aqualoan took shape, with Nick appearing to be a contributor.

However, it later became clear that he was actually the founder. When the revelations about Nick surfaced, both the protocol and its $800,000 liquidity vanished — along with Nick on March 28th.

Tanuki further revealed that Nick even tried to platform their Aqualoan project on Coingecko back in December 2024.


The project appeared to have launched in mid-November 2024, both on Twitter and more broadly. From the start, it resembled a typical DeFi initiative, complete with partnership announcements, engagement farming, and basic marketing prompts.


Previous activity on the Twitter account shows it was primarily used for basic degen activities, notably participating in giveaways. This raises the question: was Nick genuinely involved in these activities, or was the account simply purchased?
It’s difficult to determine what Nick truly intended with Aqualoan. Were they genuinely trying to build a legitimate protocol as another source of income? Was it a front for money laundering? Or was it merely a test run before launching a more sophisticated DeFi project after learning the ropes?
For now, these questions remain unanswered.
Perhaps the most astonishing aspect of this affair is how Nick attempted to infiltrate the SEAL team — a rapid-response group composed of blockchain security firms and researchers, mobilized to assist victims in the aftermath of exploits. Had they succeeded, DPRK threat actors could have gained direct access to SEAL’s strategies and intelligence, potentially allowing them to anticipate countermeasures, evade asset freezes, and refine their tactics for laundering stolen funds.
Lesson to be learned: Beware of overly solicitous individuals offering unsolicited security reports.
One last intriguing detail: Taylor Monahan uncovered a bizarre pattern in Nick’s behavior across multiple exploits — many of which were directly linked to DPRK criminal activities.
https://medium.com/media/d1a93d0036a8fa33d2cfa4c238ee49b3/hrefNick would often claim that a clear-cut exploit was merely a “rug pull” or a “rug pull or private key exploit.” Some have speculated that this could be a (weak) attempt to reshape the narrative around certain hacks — downplaying or dismissing them to divert attention from potential DPRK involvement.
However, Nick never gained enough traction or reputation to sway public opinion, especially with blockchain forensics providing evidence to the contrary.
That said, a deeper investigation into those past exploits to determine any DPRK connections is certainly worth pursuing!


HyperLiquid: The $13,5 Million Jelly Price Manipulation Debacle
Some may argue that the JELLY affair could hardly be classified as an exploit, as “code is law” and if Hyperliquid couldn’t be bothered to learn how to handle large positions and liquidations, then that’s on them.
Semantic debates aside, on paper, a trader did exploit a systemic vulnerability in Hyperliquid to try and make a profit by causing the platform to bleed.
On March 26th, a trader deposited $7 million across three accounts on Hyperliquid, with two accounts taking long positions — $2.15 million and $1.9 million on JELLY — while the third account took a $4.1 million short position.
At that time, JELLY was nothing more than a mediocre token, with a market cap barely reaching $20 million — perfectly ripe for price manipulation.
After the trader’s actions, the price of JELLY surged by over 429% within an hour, triggering the liquidation of the short position. However, the position was too large to be handled through traditional liquidation channels, so it was passed on to Hyperliquid’s market-making vault, known as the Hyperliquidity Provider (HLP) — a system originally designed to prevent extreme volatility from causing catastrophic losses.
That’s exactly what the attacker was betting on. The goal was to force the Hyperliquidity Provider (HLP) to take over the short position, keeping it open and causing significant losses as funding rates surged. This would gradually drain millions from the system. If the price of JELLY had reached $0.15374, the entire $230 million Hyperliquid vault could have been at risk of liquidation, according to Gautham, co-founder of Polynomial.

To mitigate further losses, Hyperliquid delisted the JELLY token after a “two-minute validator voting” and settled its price at $0.0095 — significantly lower than its trading price on decentralized exchanges, which was around $0.50, banking $700,000 in profit.
In the aftermath, Hyperliquid faced a double backlash: not only for its glaring vulnerabilities, such as forced position inheritance, lack of circuit breakers, small-cap tokens without position limits, and an absence of price manipulation safeguards and automated liquidations — creating a perfect environment for price manipulation — but also for its response to the hack, which highlighted its high level of centralized control.
Despite claims of decentralization, the platform’s actions, particularly its decision to delist the JELLY token and set its price at $0.0095, unfairly victimized JELLY investors, causing substantial losses for those who had purchased at much higher prices. This arbitrary decision, made without clear communication or community input, severely undermined trust in Hyperliquid.
SIR.trading DEX Breach: Exploiting Ethereum’s Transient Storage in a First-of-Its-Kind Attack
On March 30th, 2025, SIR.trading was hacked for over $335,000. While the stolen amount may seem modest, what makes this heist stand out is its modus operandi. It is, to date, the only documented exploit that leverages Ethereum’s transient storage feature, introduced with the Dencun upgrade.
The key issue is that the SIR.trading’s vault contract relied on transient storage to verify who was allowed to withdraw funds.
When the Vault contract interacts with Uniswap to execute a swap, Uniswap triggers a callback to the Vault by calling the uniswapV3SwapCallback function.
To ensure the legitimacy of the callback, the Vault temporarily stores the Uniswap pool’s address in slot 0x1 within transient storage. This storage is temporary and exists only for the duration of the callback execution.
The reason this step is crucial is that it enables the Vault to confirm that the callback is indeed originating from the expected Uniswap pool and not from a malicious actor. The Vault does this verification by checking the address stored in slot 0x1.
When the callback is executed, the Vault compares the stored address in slot 0x1 to the address of the contract that called the uniswapV3SwapCallback function. If the two addresses match, the Vault knows that the callback is legitimately from Uniswap and proceeds with the transaction. If the address doesn’t match, the Vault can reject the request, preventing unauthorized access. The attacker exploited a vulnerability in the Vault contract’s handling of Uniswap V3 swap callbacks.
In the Vault contract, the uniswapV3SwapCallback function temporarily stores the Uniswap pool’s address in slot 0x1 in transient storage for verification purposes. However, the same storage slot was later reused to store the token transfer amount, leading to a storage collision-a scenario where two different pieces of data overwrite each other in the same memory slot. The attacker was able to control the token transfer amount involved in the swap.
This allowed them to specify a transfer amount that matched the numeric representation of their crafted vanity address. In this case, the vanity address 0x00000000001271551295307acc16ba1e7e0d4281 corresponded to the token transfer amount of 95759995883742311247042417521410689. By carefully minting an exact number of tokens that matched the crafted amount, the attacker ensured that this amount would be written to slot 0x1, replacing the original Uniswap pool address.
The Vault contract, expecting to see the Uniswap pool’s address in slot 0x1, mistakenly found the attacker’s vanity address instead, since it matched the transferred token amount. To further exploit this vulnerability, the attacker deployed a malicious contract using CREATE2, ensuring that the contract’s address was identical to the crafted vanity address.
When this malicious contract then called uniswapV3SwapCallback, the Vault, upon checking slot 0x1, found the same address as the one that called the function (msg.sender), believing it to be the legitimate Uniswap pool.
Since the Vault relied on this check to verify the legitimacy of the caller, it mistakenly approved the callback from the attacker’s contract, allowing them to drain funds. This enabled the attacker to repeatedly call the callback function, siphoning off the Vault’s funds while appearing as if the calls were coming from the legitimate Uniswap pool. The entire attack was made possible by the storage collision, which allowed the attacker to overwrite a security-critical address with one they controlled.
Once the funds were stolen, the attacker laundered them through Railgun.
TL;DR:
SIR.trading relied on information from a storage slot that could be too easily altered. The hacker brute-forced a matching wallet address, used a precision-crafted exploit key, and repeatedly drained the vault by tricking the system into believing they were the legitimate Uniswap pool.
Protocols should never rely on transient storage for security-critical checks!
Bonus Story: Zklend Thief Thieved
In mid-February 2025, an attacker made off with $9.5 million after siphoning funds from the ZkLend protocol. Fast forward to March 31st — while attempting to launder the stolen funds — the attacker, who had chosen the cryptocurrency mixer Tornado Cash to obfuscate their tracks, accidentally clicked on a fake Tornado Cash website. As a result, the entire $9.5 million was funneled directly to a phishing scammer.
After this blunder, the attacker informed ZkLend of their loss and even advised them to go after the phishing scammer if they ever hoped to recover the stolen funds.

But wait — plot twist! It might all have been a staged distraction to throw investigators off Zklend’s trail. According to TornadoCashBot’s research, the Zklend attacker could actually be behind the fake Tornado Cash website!
https://medium.com/media/4e142313548ec3ba2e5b0269ad6de228/hrefOur March 2025 crypto-criminal report ends here!
See you all next month for another crypto crime report.
Until then, stay safe!
About us
Nefture is a Web3 real-time security and risk prevention platform that detects on-chain vulnerabilities and protects digital assets, protocols and asset managers from significant losses or threats.
Nefture core services includes Real-Time Transaction Security and a Threat Monitoring Platform that provides accurate exploits detections and fully customized alerts covering hundreds of risk types with a clear expertise in DeFi.

Today, Nefture proudly collaborates with leading projects and asset managers, providing them with unparalleled security solutions.
Book a demo 🤝
$124M Stolen — The March 2025 Crypto Crime Report was originally published in Coinmonks on Medium, where people are continuing the conversation by highlighting and responding to this story.

